Articles By This Author
The Buyer’s Guide to AI Usage Control
Today’s “AI everywhere” reality is woven into everyday workflows across the enterprise, embedded in SaaS platforms, browsers, copilots, extensions, and a rapidly expanding universe of shadow tools that appear faster than security teams can track. Yet most organizations still rely on legacy controls that operate far away from where AI interactions actually occur. The result […]
Infy Hackers Resume Operations with New C2 Servers After Iran Internet Blackout Ends
The elusive Iranian threat group known as Infy (aka Prince of Persia) has evolved its tactics as part of efforts to hide its tracks, even as it readied new command-and-control (C2) infrastructure coinciding with the end of the widespread internet blackout the regime imposed at the start of January 2026. “The threat actor stopped maintaining […]
Critical n8n Flaw CVE-2026-25049 Enables System Command Execution via Malicious Workflows
A new, critical security vulnerability has been disclosed in the n8n workflow automation platform that, if successfully exploited, could result in the execution of arbitrary system commands. The flaw, tracked as CVE-2026-25049 (CVSS score: 9.4), is the result of inadequate sanitization that bypasses safeguards put in place to address CVE-2025-68613 (CVSS score: 9.9), another critical […]
Microsoft Develops Scanner to Detect Backdoors in Open-Weight Large Language Models
Microsoft on Wednesday said it built a lightweight scanner that it said can detect backdoors in open-weight large language models (LLMs) and improve the overall trust in artificial intelligence (AI) systems. The tech giant’s AI Security team said the scanner leverages three observable signals that can be used to reliably flag the presence of backdoors […]
DEAD#VAX Malware Campaign Deploys AsyncRAT via IPFS-Hosted VHD Phishing Files
Threat hunters have disclosed details of a new, stealthy malware campaign dubbed DEAD#VAX that employs a mix of “disciplined tradecraft and clever abuse of legitimate system features” to bypass traditional detection mechanisms and deploy a remote access trojan (RAT) known as AsyncRAT. “The attack leverages IPFS-hosted VHD files, extreme script obfuscation, runtime decryption, and in-memory
China-Linked Amaranth-Dragon Exploits WinRAR Flaw in Espionage Campaigns
Threat actors affiliated with China have been attributed to a fresh set of cyber espionage campaigns targeting government and law enforcement agencies across Southeast Asia throughout 2025. Check Point Research is tracking the previously undocumented activity cluster under the moniker Amaranth-Dragon, which it said shares links to the APT 41 ecosystem. Targeted countries include Cambodia,
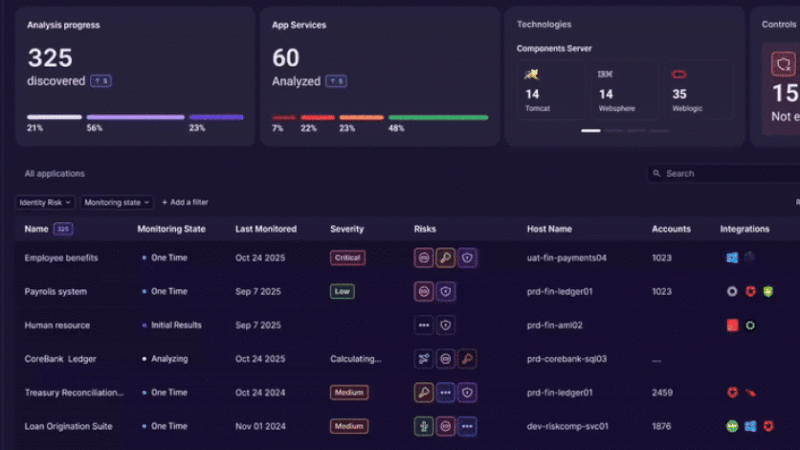
Orchid Security Introduces Continuous Identity Observability for Enterprise Applications
An innovative approach to discovering, analyzing, and governing identity usage beyond traditional IAM controls. The Challenge: Identity Lives Outside the Identity Stack Identity and access management tools were built to govern users and directories. Modern enterprises run on applications. Over time, identity logic has moved into application code, APIs, service accounts, and custom authentication
The First 90 Seconds: How Early Decisions Shape Incident Response Investigations
Many incident response failures do not come from a lack of tools, intelligence, or technical skills. They come from what happens immediately after detection, when pressure is high, and information is incomplete. I have seen IR teams recover from sophisticated intrusions with limited telemetry. I have also seen teams lose control of investigations they should […]
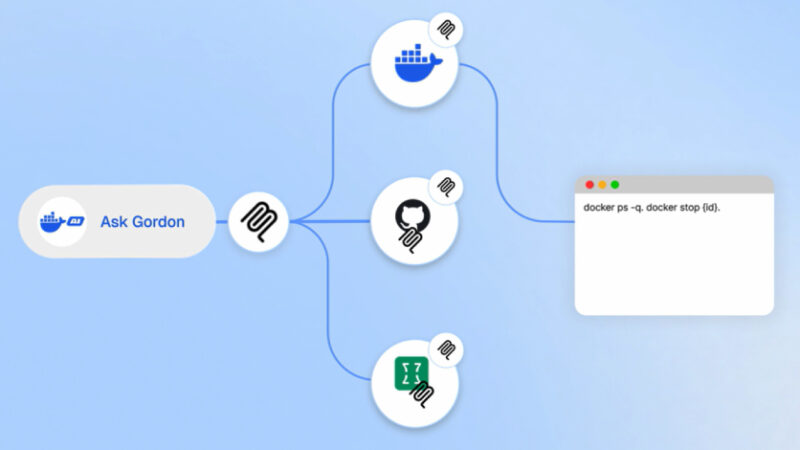
Docker Fixes Critical Ask Gordon AI Flaw Allowing Code Execution via Image Metadata
Cybersecurity researchers have disclosed details of a now-patched security flaw impacting Ask Gordon, an artificial intelligence (AI) assistant built into Docker Desktop and the Docker Command-Line Interface (CLI), that could be exploited to execute code and exfiltrate sensitive data. The critical vulnerability has been codenamed DockerDash by cybersecurity company Noma Labs. It was addressed by
[Webinar] The Smarter SOC Blueprint: Learn What to Build, Buy, and Automate
Most security teams today are buried under tools. Too many dashboards. Too much noise. Not enough real progress. Every vendor promises “complete coverage” or “AI-powered automation,” but inside most SOCs, teams are still overwhelmed, stretched thin, and unsure which tools are truly pulling their weight. The result? Bloated stacks, missed signals, and mounting pressure to […]