CISA Flags Actively Exploited Digiever NVR Vulnerability Allowing Remote Code Execution
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added a security flaw impacting Digiever DS-2105 Pro network video recorders (NVRs) to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. The vulnerability, tracked as CVE-2023-52163 (CVSS score: 8.8), relates to a case of command injection that allows post-authentication remote code
New MacSync macOS Stealer Uses Signed App to Bypass Apple Gatekeeper
Cybersecurity researchers have discovered a new variant of a macOS information stealer called MacSync that’s delivered by means of a digitally signed, notarized Swift application masquerading as a messaging app installer to bypass Apple’s Gatekeeper checks. “Unlike earlier MacSync Stealer variants that primarily rely on drag-to-terminal or ClickFix-style techniques, this sample adopts a more
Nomani Investment Scam Surges 62% Using AI Deepfake Ads on Social Media
The fraudulent investment scheme known as Nomani has witnessed an increase by 62%, according to data from ESET, as campaigns distributing the threat have also expanded beyond Facebook to include other social media platforms, such as YouTube. The Slovak cybersecurity company said it blocked over 64,000 unique URLs associated with the threat this year. A […]
Attacks are Evolving: 3 Ways to Protect Your Business in 2026
Every year, cybercriminals find new ways to steal money and data from businesses. Breaching a business network, extracting sensitive data, and selling it on the dark web has become a reliable payday. But in 2025, the data breaches that affected small and medium-sized businesses (SMBs) challenged our perceived wisdom about exactly which types of businesses […]
SEC Files Charges Over $14 Million Crypto Scam Using Fake AI-Themed Investment Tips
The U.S. Securities and Exchange Commission (SEC) has filed charges against multiple companies for their alleged involvement in an elaborate cryptocurrency scam that swindled more than $14 million from retail investors. The complaint charged crypto asset trading platforms Morocoin Tech Corp., Berge Blockchain Technology Co., Ltd., and Cirkor Inc., as well as investment clubs AI […]
Italy Fines Apple €98.6 Million Over ATT Rules Limiting App Store Competition
Apple has been fined €98.6 million ($116 million) by Italy’s antitrust authority after finding that the company’s App Tracking Transparency (ATT) privacy framework restricted App Store competition. The Italian Competition Authority (Autorità Garante della Concorrenza e del Mercato, or AGCM) said the company’s “absolute dominant position” in app distribution allowed it to “unilaterally impose”
Two Chrome Extensions Caught Secretly Stealing Credentials from Over 170 Sites
Cybersecurity researchers have discovered two malicious Google Chrome extensions with the same name and published by the same developer that come with capabilities to intercept traffic and capture user credentials. The extensions are advertised as a “multi-location network speed test plug-in” for developers and foreign trade personnel. Both the browser add-ons are available for download […]
INTERPOL Arrests 574 in Africa; Ukrainian Ransomware Affiliate Pleads Guilty
A law enforcement operation coordinated by INTERPOL has led to the recovery of $3 million and the arrest of 574 suspects by authorities from 19 countries, amidst a continued crackdown on cybercrime networks in Africa. The coordinated effort, named Operation Sentinel, took place between October 27 and November 27, 2025, and mainly focused on business […]
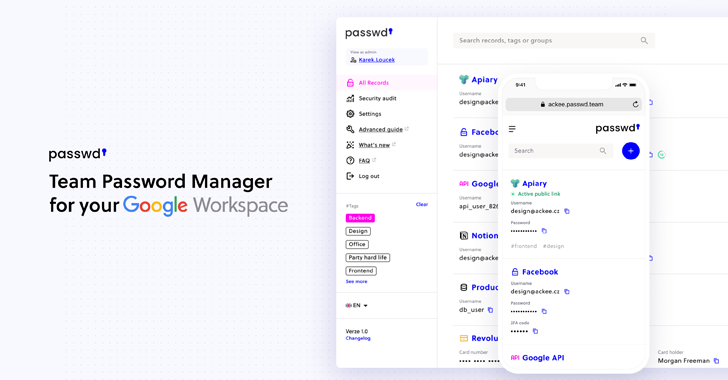
Passwd: A walkthrough of the Google Workspace Password Manager
Passwd is designed specifically for organizations operating within Google Workspace. Rather than competing as a general consumer password manager, its purpose is narrow, and business-focused: secure credential storage, controlled sharing, and seamless Workspace integration. The platform emphasizes practicality over feature overload, aiming to provide a reliable system for teams that already rely
U.S. DoJ Seizes Fraud Domain Behind $14.6 Million Bank Account Takeover Scheme
The U.S. Justice Department (DoJ) on Monday announced the seizure of a web domain and database that it said was used to further a criminal scheme designed to target and defraud Americans by means of bank account takeover fraud. The domain in question, web3adspanels[.]org, was used as a backend web panel to host and manipulate […]